The BGP (protocol) has been on my mind the last few weeks.
It boggles my mind how fragile the web is that we all operate on, more specifically that we rely on BGP TCP/IP to maintain connections between two or more autonomous system routers.
BGP is simply put, is the Internet’s greatest weakness.
OK, so what is BGP?
According to he RFC (last pub 2006)
The primary function of a BGP speaking system is to exchange network
reachability information with other BGP systems.
GP-4 provides a set of mechanisms for supporting Classless Inter-
Domain Routing (CIDR) [RFC1518, RFC1519]. These mechanisms include
support for advertising a set of destinations as an IP prefix and
eliminating the concept of network “class” within BGP. BGP-4 also
introduces mechanisms that allow aggregation of routes, including
aggregation of AS paths.
Attacking it?
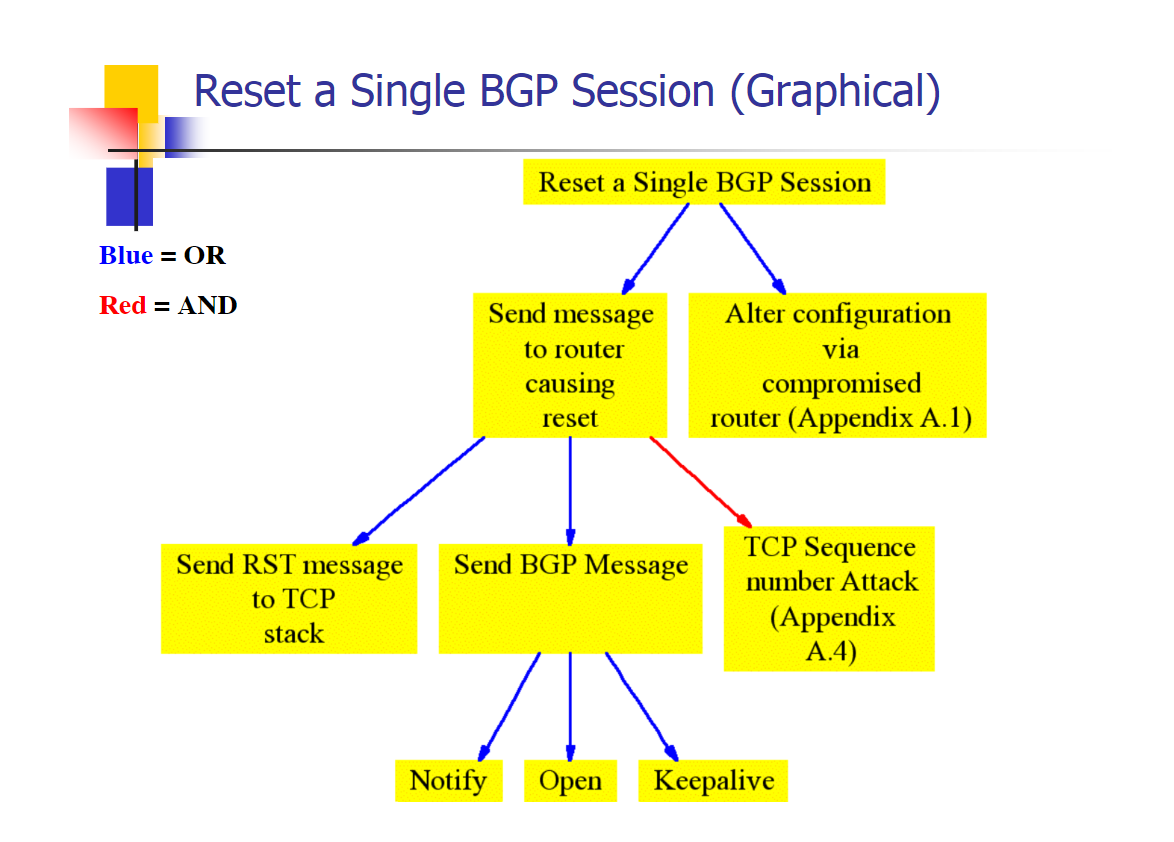
Acording to Sean Convery (cisco) from his blackhat talk in 2003 below is how you shoudld go about it (kindof, we will go into more detail later):
Reset a single BGP session to control a block of IP’s and corrupt other BGP routers. The easiest way to do this would be to gain lawful access to a BGP backbone, e.g. become an engineer for a site, or befriend someone who has access.
OK, so?
Well from all my readings and research, it seems like this is where the bottom foundational layer of trust the WHOLE internet lies. Without the BGP, there is no CIDR, without CIDR there is no IP’s, without IP’s there is no DNS, without DNS there is no websites, without websites many services simply die and cue end of the world scenarios.
Why was this on my mind? Well i’ve been curious about it before, but recently i have been thinking about the unseen weaknesses in CryptoCurrencies. If the internet breaks, or a government decides to hard fork/cut access and limit it, then crypto as we know it is valueless. It simply looses ALL value.
Crypto other than a few projects all works from HTTP, ip, tor, IPFS etc.. which relies on IP addressing. When the very foundation of these protocols is in question, then the whole behemoth is in danger. BGP simply is the biggest threat to modern crypto economies.
tl;dr: An old protocol (BGP) run by potentially vulnerable companies, could break the internet by issuing bad or malicious commands.
Further reading:
BGP RFC
on wired
Cisco press
techopedia
Network computing.com